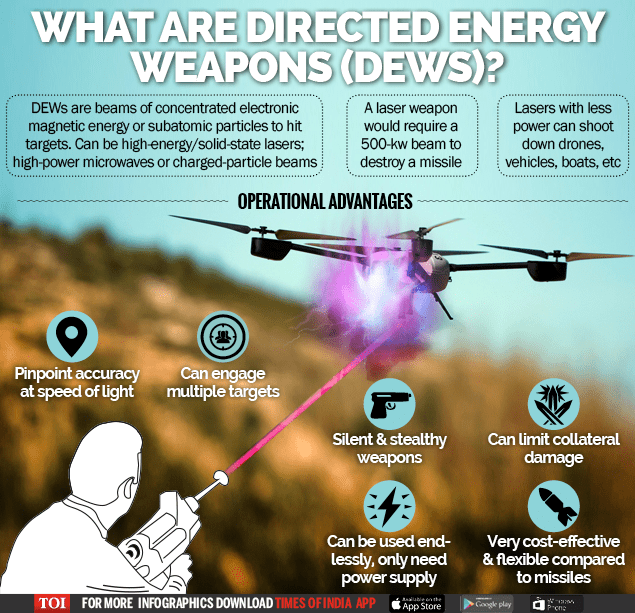
DEWs explained…



For the first time, scientists have created embryos that are a mix of human and monkey cells.
The embryos, described Thursday in the journal Cell, were created in part to try to find new ways to produce organs for people who need transplants, said the international team of scientists who collaborated in the work. But the research raises a variety of concerns.
“My first question is: Why?” said Kirstin Matthews, a fellow for science and technology at Rice University’s Baker Institute. “I think the public is going to be concerned, and I am as well, that we’re just kind of pushing forward with science without having a proper conversation about what we should or should not do.”
Still, the scientists who conducted the research, and some other bioethicists defended the experiment.
Google is ramping up its monopoly on tracking users with a new system called FloC, or Federated Learning of Cohorts”. It is currently in test mode with some Chrome users, and you can quickly find out if you are being “FloCed” by going to EFF’s AmIFloced.org site.
Google is running a Chrome “origin trial” to test out an experimental new tracking feature called Federated Learning of Cohorts (aka “FLoC”). According to Google, the trial currently affects 0.5% of users in selected regions, including Australia, Brazil, Canada, India, Indonesia, Japan, Mexico, New Zealand, the Philippines, and the United States. This page will try to detect whether you’ve been made a guinea pig in Google’s ad-tech experiment.
Cell phone injury lawsuits have existed for many years in the U.S. and worldwide (see 1, 2, 3, 4).
In the U.S. defense attorneys are currently trying to stop scientific testimony from being allowed in one case.
From Microwave News:
As expected, defense lawyers have asked the DC court to not allow Christopher Portier to be an expert witness in this case.
In a filing yesterday, the team representing the cell phone industry, argued that, “[A]llowing a new expert four months before the long-planned Daubert hearing would disrupt the existing schedule and unfairly prejudice Defendants.”
The filing was signed by Terry Dee of McDermott Will & Emery in Chicago on behalf of himself and 37 other lawyers at 23 law firms.
Portier was retained by the plaintiff attorneys in March 15, 2015 with the payment of a $5,000 retainer. It is not clear why his report was filed last month, close to six years later.
No word on when the judge may rule on Portier’s participation.
Two aerospace firms accomplished an industry first on Monday, as a small Northrop Grumman spacecraft docked successfully with an active Intelsat satellite to provide service and extend its life.
Intelsat’s IS-10-02 satellite is nearly 18 years old, and operating well past its expected lifespan, but the Northrop Grumman-built spacecraft called MEV-2 will add another five years of life to IS-10-02, essentially re-fueling the satellite and giving it a new engine for control.
The companies hit a milestone in the growing business of servicing satellites while in space.
“Today’s successful docking of our second Mission Extension Vehicle further demonstrates the reliability, safety and utility of in-space logistics,” Tom Wilson, vice president of Nothrop Grumman’s strategic space systems said in a statement. “The success of this mission paves the way for our second generation of servicing satellites and robotics, offering flexibility and resiliency for both commercial and government satellite operators, which can enable entirely new classes of missions.”
Pentagon scientists have unveiled a microchip implant that can be inserted into the skin and can sense the COVID-19 virus in a person’s bloodstream before they become sick.
They showed reporters on CBS’ “60 Minutes” how the device works. It is inserted into the skin and supposedly senses the COVID-19 virus, and when connected to a dialysis machine, can flush the virus out of the body before an individual gets sick.
‘You put it underneath your skin and what that tells you is that there are chemical reactions going on inside the body, and that signal means you are going to have symptoms tomorrow,” said former colonel Matt Hepburn, who now works for the Defense Advanced Research Projects Agency (DARPA).
While this technology may be highly advanced and perhaps effective at stopping the spread of COVID-19, the proliferation of such microchip solutions risks the creation of a dystopian environment that puts anything George Orwell prophesied to shame.

The Spanish firm Grifols helped set off a kerfuffle last year when it, along with other firms, offered nearly double the going price for blood donations for a COVID-19 treatment trial. Brigham Young University in Idaho had to threaten some enterprising students with suspension to keep them from intentionally trying to contract COVID-19. The trial failed, however, and now the Barcelona-based firm is hoping to extract something far more valuable from the plasma of young volunteers: a set of microscopic molecules that could reverse the process of aging itself.
Earlier this year, Grifols closed on a $146 million-deal to buy Alkahest, a company founded by Stanford University neuroscientist Tony Wyss-Coray, who, along with Saul Villeda, revealed in scientific papers published in 2011 and 2014 that the blood from young mice had seemingly miraculous restorative effects on the brains of elderly mice. The discovery adds to a hot area of inquiry called geroscience that “seeks to understand molecular and cellular mechanisms that make aging a major risk factor and driver of common chronic conditions and diseases of older adulthood,” according to the National Institutes of Health. In the last six years, Alkahest has identified more than 8,000 proteins in the blood that show potential promise as therapies. Its efforts and those of Grifols have resulted in at least six phase 2 trials completed or underway to treat a wide range of age-related diseases, including Alzheimer’s and Parkinson’s.
Alkahest and a growing number of other geroscience health startups signal a change in thinking about some of the most intractable diseases facing humankind. Rather than focusing solely on the etiology of individual diseases like heart disease, cancer, Alzheimer’s and arthritis—or, for that matter, COVID-19—geroscientists are trying to understand how these diseases relate to the single largest risk factor of all: human aging. Their goal is to hack the process of aging itself and, in the process, delay or stave off the onset of many of the diseases most associated with growing old
Transhumanists have hyped the new religion of high technology for decades now. The basic idea, fairly prevalent in Silicon Valley, is that rapid advances in scientific knowledge and tech innovation will culminate in our de facto omniscience and omnipotence. Even though humanity is lost in a godless cosmos, digital devices will allow us to transcend our ape-like forms.
As Google’s Ray Kurzweil famously quipped, “Does God exist? I would say, ‘Not yet.’”
One day soon, they promise, we’ll use artificial intelligence to overcome the limits of our meat-based cognition. According to Yuval Noah Harari’s 2015 best-seller “Homo Deus,” computer programmers will realize the age-old fantasies of shamans and prophets by creating a virtual version of the spiritual realm. These Davos darlings are certain “God is dead,” but Google still wants to patent His best ideas.
Ultimately, they hope to replicate the fabric of ourselves in cyberspace, where we can all live happily ever after — that is, until the electricity goes out. A recent paper by Russian transhumanist Alexey Turchin argues this “digital resurrection” is not only possible but necessary to reach our full potential. We just need enough power — both computational and electric — to create a virtual afterlife and then keep it running.
For Turchin, the solution is to construct a Dyson Sphere around the sun — a megastructure 186 million miles in diameter that’s covered in solar panels to capture the dying star’s rays. That way, we can run the gargantuan super-computers required to house our digital selves. Sounds easy enough, I suppose. Maybe we can fill the potholes in the road while we’re at it.
You must be logged in to post a comment.